If you’re wondering what Zama is and why it’s being described as one of the most important privacy projects in crypto today, you’re in the right place. Zama is a protocol that enables applications to operate on encrypted data without exposing sensitive information on public blockchains. Most blockchains are transparent by default. Anyone can see balances, transactions, and contract activity. That openness is powerful, but it also limits real-world use cases where privacy matters.
Zama changes that by enabling confidential smart contracts that keep data private while still running on-chain. So, instead of choosing between transparency and privacy, Zama’s technology allows developers and users to have both. This guide explains what Zama is, how the Zama network works, and what the ZAMA token does. You’ll also get to understand where the Zama ecosystem fits into the future of blockchain.
What Is Zama Confidentiality Protocol?
Zama confidentiality protocol is a system designed to keep sensitive data private on public blockchains through Fully Homomorphic Encryption. It allows smart contracts to process encrypted information without revealing it to the network, validators, or outside observers. In short, Zama lets apps “see” and compute data without ever reading it in plain text.
Most traditional blockchains act like open ledgers. Once you publish data, it becomes visible to everyone forever. Zama protocol changes this model by keeping inputs, outputs, and internal logic private when needed. Only authorized users can access the decrypted results, often through threshold decryption mechanisms.
This enables the development of privacy-preserving apps while still benefiting from the openness and security that blockchains offer.
Who is Zama Best for?
Zama is best for a wide range of users across Web3 and beyond:
- Developers who want to build apps that require privacy by default.
- Businesses handling sensitive user or financial data.
- DeFi platforms that need confidential balances or strategies.
- Institutions exploring blockchain without exposing internal data.
- Web3 users who want privacy without giving up usability.
If an app needs to protect raw user data while still running on a public chain, Zama is built for that.
How Does Zama Network Work?
The Zama network works by using advanced encryption techniques that allow computations to happen on encrypted data directly. That means data stays coded from the moment it enters the system until the authorized user reads the result.
Here’s a simple flow of what happens:
- A user submits encrypted data to a smart contract.
- The contract runs calculations without unlocking the data.
- The output remains encrypted on-chain.
- Only approved users can decrypt and view the final result using threshold decryption.
At no point does sensitive information become publicly visible. This removes the usual tradeoff between privacy and transparency that exists on most blockchains. Unlike traditional privacy methods that hide data off-chain, Zama keeps everything on-chain and verifiable using confidential computing.
Zama is also built to work alongside existing blockchains rather than replace them. Developers can add confidentiality to current networks without changing how the rest of the ecosystem operates.
Key Features of the Zama Protocol
Zama stands out because it focuses on practical, usable privacy rather than theoretical complexity. The core features that define the protocol are:
1. End-to-End Encrypted Smart Contracts
Zama enables smart contracts that keep sensitive data private at every stage. Information enters the contract in encrypted form and leaves the same way, without ever being exposed publicly.
This means details such as account balances, user identities, or business logic do not appear on the blockchain for everyone to see. The contract can still function as expected, but without revealing what it is working with.
Even the network participants who help run the contract cannot view the underlying data. Only authorized users can access the final results. These protections enable the creation of decentralized exchanges with enhanced privacy, where sensitive trading data stays hidden.
2. Programmable Confidentiality
Privacy on Zama is flexible, not all-or-nothing. Developers can choose exactly what stays private and what remains visible, depending on the app’s needs thanks to confidential computing capabilities.
This selective approach allows for practical setups such as:
- Private balances that can still be verified without revealing exact amounts.
- Hidden inputs that allow users to protect sensitive data while showing final outcomes.
- Controlled data sharing between specific parties without exposing information publicly.
Programmable confidentiality enables the design of apps that meet real business and user requirements, where transparency and privacy must coexist.
3. Fully Homomorphic EVM (fhEVM)
Zama is designed to work with the Ethereum ecosystem via an EVM-compatible environment known as fhEVM. It’s a specialized smart contract engine that allows developers to build confidential smart contracts while using tools and workflows they already know.
Instead of starting from scratch, teams can adapt existing applications to support encrypted data. That shortens development time and reduces mistakes. Moreover, it makes it easier to integrate privacy features into real-world products on the Zama network.
4. Cross-Chain Composability
Zama is built to work across multiple blockchains, not just a single network. Apps using Zama can interact with other protocols, assets, and services already active in Web3. This means privacy does not lock apps into a closed system.
Developers can add confidentiality while still connecting to the existing ecosystem. Such an approach allows users to move value, share data, and interact across chains without exposing sensitive information.
5. Developer-Friendly Tooling
Zama offers easy-to-use tools that help developers build confidential apps without friction. Its libraries, SDKs, and documentation are designed to be practical and easy to follow, even for teams new to privacy-focused development.
Even though the underlying system relies on Torus Fully Homomorphic Encryption (TFHE), Zama lowers the barrier to entry. Privacy becomes a realistic option for everyday applications, not just highly specialized projects.
Zama Products and Technologies
The Zama ecosystem includes several components that make the Zama confidential blockchain protocol applications possible:
- fhEVM: A specialized smart contract engine that allows developers run smart contracts confidentially using familiar Ethereum tools. It ensures privacy while keeping the coding experience intuitive.
- Zama protocol: The core system that develops Fully Homomorphic Encryption (FHE) into usable infrastructure. It forms the foundation for all private operations on the network.
- Cryptographic libraries: Ready-made tools that handle encryption and privacy tasks securely. Built on Torus Fully Homomorphic Encryption, they simplify implementing confidentiality without deep cryptography knowledge.
- Developer SDKs: Resources and guides that make it faster and easier to build on Zama. They help teams test, deploy, and debug confidential apps efficiently.
- Integration tools: Help connect Zama to existing blockchains and applications smoothly. Through them, apps can work across different networks without losing privacy.
Together, these products provide a complete stack that lets developers build secure, private blockchain applications without starting from scratch.
Zama Use Cases in Web3 and Beyond

Zama is versatile. Its design supports a wide range of applications, both in crypto and real-world settings.
- Decentralized finance (DeFi): Zama allows users to hide balances, transaction amounts, and trading strategies. This opens the door to more secure trading environments, including privacy-preserving perpetual DEXs that protect positions and reduce unwanted market exposure.
- Payments: Users can make confidential transfers that hide amounts from the public, offering privacy similar to traditional banking while staying on-chain.
- Identity systems: Help protect personal information with encrypted data while still allowing verification. Users stay in control of what they share.
- Enterprise and institutions: Zama enables privacy for tokenized real-world assets, allowing ownership and transfers to be recorded on-chain without exposing confidential financial or business data.
- Sealed bid auctions: Through Zama, firms can run auctions where bids remain hidden until the winner is revealed. It ensures fairness and confidentiality.
- Governance and infrastructure: Zama enables private voting or decision-making within decentralized autonomous organizations (DAOs), without revealing individual choices publicly.
- Asset tokenization: Keep details about tokenized assets, ownership, or transactions confidential while still verifiable on-chain.
Beyond Web3, Zama’s technology can support healthcare records, voting systems, and data marketplaces where confidentiality is critical. Zama is also used in AI and machine learning, allowing developers to train models with encrypted data without exposing the raw data.
What Is the ZAMA Token Used For?
The ZAMA token is used for:
- Paying for network usage and encrypted computations
- Rewarding participants such as validators, developers, and contributors who maintain and grow the protocol fees.
- Governance and decision-making that allow token holders to participate in shaping the network’s future and protocol upgrades.
- Aligning ecosystem stakeholders for long-term success
Unlike tokens designed purely for speculation, ZAMA supports real-world applications of confidential blockchain technology.
ZAMA Token Overview
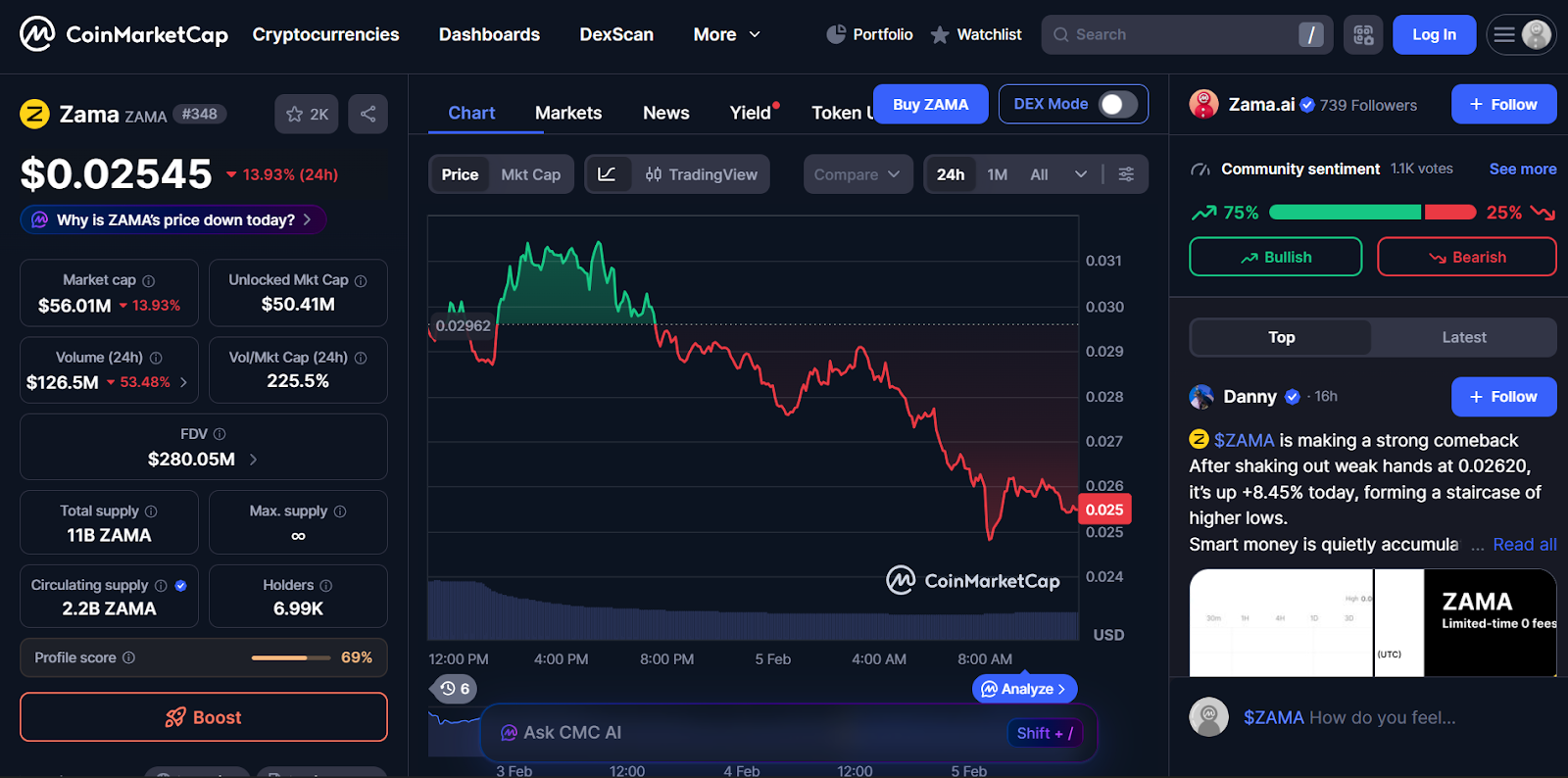

The ZAMA token is the native asset of the Zama network. It was launched on February 2, 2026, following a sealed-bid Dutch auction that gave many early participants a chance to acquire tokens before trading began on major exchanges.
It’s more than just a utility token. ZAMA helps align the interests of developers building applications, users running smart contracts, and infrastructure providers maintaining the network. When more people use confidential smart contracts, demand for ZAMA naturally grows, supporting network activity.
The token’s supply and distribution are designed carefully to encourage steady, sustainable growth:
- Total supply is fixed: There will only be 11 billion ZAMA tokens. This cap helps keep the supply predictable as the network grows.
- Circulating supply at launch: At the token generation event, about 2.2 billion ZAMA (roughly 20%) were in circulation. This gave the network early liquidity while leaving room for future growth.
- Balanced distribution: The remaining tokens are allocated across categories like team, treasury, growth, and investors. Each group has vesting schedules that encourage long-term commitment instead of quick selling.
The way tokens are released and rewarded ties users and developers around long‑term success, not short‑term hype.
Zama vs Other Privacy Solutions
Unlike many privacy tools that operate separately from network consensus, Zama is designed to work alongside modern proof-of-stake blockchains. Here’s how it compares to other approaches:
| Feature | Zama | Traditional Privacy Blockchains | Off-Chain Privacy Tools |
| Data privacy | End-to-end encrypted on-chain | Private transactions, but limited contract privacy | Data is kept off-chain, but contracts are often transparent |
| Smart contract use | Supports confidential smart contracts directly | Often limited to token transfers of private balances | Not native, so it requires extra integration |
| Programmable privacy | Developers can choose which parts of an app stay private | Usually all-or-nothing privacy | Limited flexibility |
| Ease of integration | EVM-compatible (fhEVM), with developer tools available | Separate environments so there is a learning curve | Needs custom solutions for on-chain interactions |
| Cross-chain support | Designed for multiple chains and composable apps | Usually chain-specific | Difficult to integrate with multiple chains |
| Real-world use | Payments, DeFi, identity, enterprise, and AI applications | Mostly DeFi or simple token privacy | Often experimental use cases (niche) |
Zama makes privacy practical and flexible. Other privacy solutions may offer strong anonymity, but they often trade off usability, speed, or developer friendliness.
Zama Roadmap and Future Outlook
Zama is moving from research into real-world use, and its roadmap reflects that shift. The project’s public testnet is already live. This has allowed developers to experiment with confidential contracts and learn how the network operates.
A major milestone was the launch of the Ethereum mainnet in late 2025, when the first confidential transfers using Zama’s technology occurred. Building on that foundation, the team plans to expand support to other environments in 2026. In the first half of 2026, more EVM-compatible blockchains will gain Zama’s privacy layer, followed by support for Solana later in the year.
Beyond adding more chains, Zama is also focused on improving overall performance and network reach. Work is underway to make encrypted operations faster and more scalable, including moving from CPU to GPU computing and eventually using custom hardware, such as FHE ASICs (specialized chips) to boost throughput.
Part of the roadmap also includes expanding who can operate the network. A set of genesis operators, who are independent organizations handling key network functions, has already been established. Over time, more participants will be able to join, helping make the system more resilient and decentralized.
Looking ahead, Zama’s long-term vision is to make confidentiality a standard feature of blockchain, not a niche add-on. As more applications and services require privacy, Zama aims to be the foundation that supports those needs. With each new integration and performance improvement, the network moves closer to this broader goal.
Conclusion
Zama tackles one of blockchain’s biggest challenges: how to use sensitive data without exposing it publicly. Its protocol makes it possible to run confidential smart contracts and process encrypted inputs. In return, this has opened the door to real-world applications in finance, identity, enterprise, and beyond.
With a growing ecosystem, developer-friendly tools, and EVM compatibility, Zama is not just a research project. It’s becoming a practical foundation for privacy-focused blockchain solutions. The network shows how confidentiality and transparency can coexist. As such, it has given developers and organizations the flexibility to build secure applications without compromising user trust.
For anyone exploring Web3, whether you’re a developer, business, or user, Zama represents a step toward usable, private, and secure blockchain systems. Its technology points to a future where privacy is a standard feature, not an afterthought. With Zama, sensitive data stays secure while still benefiting from the advantages of decentralization.
FAQs
Yes, Zama has a native token called ZAMA. The ZAMA token is used within the Zama ecosystem to pay for network operations, reward participants, and support governance decisions.
Zama itself is not a standalone blockchain. Instead, it is a confidentiality protocol that can work on top of existing blockchains. This allows developers to add privacy features, such as encrypted smart contracts, to public chains without having to build a new blockchain from scratch. Zama focuses on privacy and usability while leveraging the security of established networks.
Yes, Zama can run on Ethereum and other EVM-compatible chains through its fhEVM environment. With this, developers can build confidential smart contracts using tools and languages they are already familiar with, while benefiting from Zama’s privacy features. It makes adding confidentiality simple and fast without starting from zero.
Zama does not replace zero-knowledge proofs. It complements them, instead. The protocol uses advanced cryptography to keep data private while enabling computations over encrypted data. Developers can still leverage ZKPs when needed, but Zama offers a broader framework for confidential smart contracts and encrypted data processing.